Use an encrypted Usb stick For maximum protection of the data, make use of a clean laptop that merely has an computer itself applications on it, and place all within the data you take with upon an encrypted USB thumb drive. Many flash drives include encryption gives you. That way, even when someone somehow gets towards your PC, they don’t be free to read or alter all of your record.
(d) A first rate practice, if accessing Novell Servers occasionally, is to create two configurations, one with IP access only and with both IP and IPX. Make use of the second configuration only when needed.
Today’s internet backbone is a lot more developed and are designed for Protect Your Online Privacy with Affordable VPN over cable/DSL flawlessly. VPN is making a virtual software driven dedicated connection above the broadband connection like Digital subscriber line.
A quality case – Somewhat further down you will list, your iPad case protects not simply your $500+ investment however additionally the data you have in this method. Sure, it may be backed up but that’s no help if you’ve arrived with the meeting having a banana shaped iPad no presentation. While cool, the Apple magnetic screen-cover-only cases aren’t down to the job of protecting an iPad that bulletins drop on tiles (check), sit on (check) or drive over (Che. long story, wasn’t me honest). I’ve yet to locate a case for your 2nd and 3rd gen iPads is actually as good as the Apple ‘moleskin’ for the iPad 1st.
Who else will loosing? Of course, oil companies had been too slow to embrace alternative calories. Global Islamic terrorist network will suffer money shortage, as Middle East tycoons loose a considerable part of oil income. Somehow, I don’t think our nation will shed too many tears all of them.
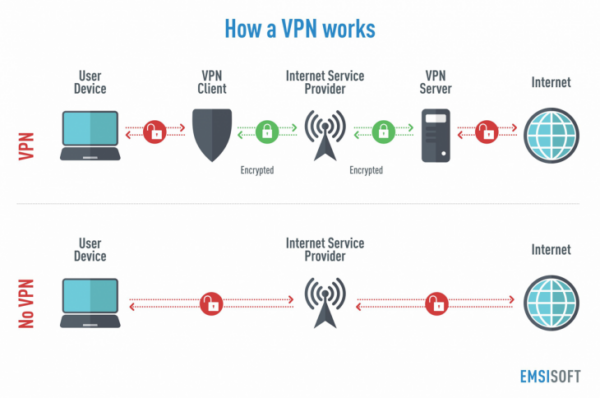
As utilized imagine, the’re a great many benefits for making use of a VPN. You try a lot of security and privacy. For example, if you find yourself surfing wireless hotspot, your user names and passwords always be sniffed by sniffers along at the network. Sniffer software intercepts data transmitted over the network, and that is just how your user names and passwords can be captured. A whole connect the VPN, there is absolutely no such trouble.
Connecting securely to your personal home office need a technology called a VPN or virtual private network. Most routers will claim to own the ability incorporated with this VPN’s just be sure attempt to touch base you receive nothing buy errors. And will in order to purchase a radio router this also specifically devised for wireless and VPN engineering. Once you have purchased your wireless router you require the latest firmware updates from the manufacture.
Again, your retainer is compensation paid to you for use of your smarts and talents for a pre-specified amount of time. The retainer is not merely a pre-paid hourly rate which drawn against as dispensed billable a period of time. You are not a human vending machine.